https://sputnikglobe.com/20211117/hackers-reportedly-go-on-global-hacking-spree-targeting-media-governments-using-israeli-spyware-1090804917.html
Hackers Reportedly Go on Global Hacking Spree Targeting Media, Governments Using Israeli Spyware
Hackers Reportedly Go on Global Hacking Spree Targeting Media, Governments Using Israeli Spyware
Sputnik International
Israel’s US ally recently slapped sanctions on NSO Group – makers of the infamous spyware Pegasus, after the spyware was shown to have been used by governments... 17.11.2021, Sputnik International
2021-11-17T14:01+0000
2021-11-17T14:01+0000
2023-05-28T15:16+0000
israel
hacking
middle east
united kingdom (uk)
https://cdn1.img.sputnikglobe.com/img/07e6/03/16/1094083537_0:0:471:265_1920x0_80_0_0_68a55ba175b36479745bc2d8e1ee81c1.jpg
A computer hacking tool developed by Candiru, a Tel Aviv-based surveillance and cyberespionage technology firm catering to government clients, has been used to systematically attack websites in the UK, Iran, Syria and Yemen, ESET, a Slovak internet security company has discovered.“The victimized websites belong to media outlets in the UK, Yemen, and Saudi Arabia, as well as Hezbollah; to government institutions in Iran (Ministry of Foreign Affairs), Syria (including the Ministry of Electricity), and Yemen (including the Ministries of Interior and Finance); to internet service providers in Yemen and Syria; and to aerospace/military technology companies in Italy and South Africa. The attackers also created a website mimicking a medical trade fair in Germany,” ESET said in a comprehensive analysis published Tuesday.The ultimate goal of the attacks were said to include collecting IP geolocation data and the targeted computer’s system information, and, if desired, to enable attackers to hijack the infected machines.The affected websites include the Middle East Eye – a UK-based news site focused on Middle Eastern affairs, the site of Hezbollah’s Al Manar television channel, and Yemen’s Almasirah – a media outlet affiliated with the Houthis. thesaudireality.com, a Saudi dissident website critical of the monarchy, was also reportedly among those attacked.Among other targets were Piaggio Aerospace, an Italian arms maker, and Denel, a South African aerospace and military tech giant.Of the 21 websites attacked, eight are based in Yemen, three are Syrian, and three are operated by Hezbollah.The Middle East Eye announced that it was considering legal action against parties which it suspects of involvement in the attacks in the attacks, without elaborating on who it believes may be responsible.In a report in July, the University of Toronto’s Citizen Lab software developer reported, citing a lawsuit brought by a former Candiru employee, that the company’s clients include the governments of Saudi Arabia, the United Arab Emirates and Qatar, as well as Singapore and Uzbekistan.In the wake of ESET’s reporting, a Candiru spokesperson assured Forbes that the company itself does not carry out attacks on clients’ behalf, and that it does not have any knowledge about how clients use its tools. “The company is selling its products to government agencies only…the company and its product don’t hack websites,” the spokesperson said.Candiru was founded in 2014, and is named after a parasitic catfish. The company is so secretive that it does not have public website, and little information exists online about its earnings, employees, and other basic information. The firm is only allowed to export its products if Israel’s Defence Ministry grants it an export license.The source or sources of the attacks are unclear. They reportedly ceased abruptly in mid-2021, after Citizen Lab researchers issued a report on Candiru’s use by governments to target journalists and activists in Armenia, Iran, Israel, Lebanon, Yemen, Spain, the UK, and Turkey, and to have been operated from inside nations including Hungary, Indonesia, Israel, Saudi Arabia, and the United Arab Emirates.The US Commerce Department surprisingly slapped Candiru and its more famous cousin, NSO Group, with sanctions earlier this month. NSO Group’s Pegasus spyware, which can infect phones using ‘zero clicks’ (i.e. without any user interaction), and is impossible to remove, came into the public spotlight in July after the non-profits Forbidden Stories and Amnesty International shared a list of over 50,000 people whose phones were targeted. The software is capable of hijacking a phone’s camera and microphones, essentially turning it into a mobile spying device, and allows operators to access users’ contacts, message and call history, and more.The victims of the military-grade spyware package reportedly included over a dozen world leaders, among them French President Emmanuel Macron, Iraqi President Barham Salih, South African President Cyril Ramaphosa, and others, as well as a bevy of former heads of state and government, UN and WHO officials, journalists, dissidents, and opposition politicians.NSO Group defended itself by claiming that it sells its spyware to governments only for use against terrorists and criminals, suggesting that Pegasus had saved “tens of thousands of lives.” Instead, it was used by governments to target foreign adversaries and domestic opponents, with Mexican drug cartels also reportedly getting their hands on the software and using it to intimidate journalists.
https://sputnikglobe.com/20211031/iran-zionist-regime-the-americans-behind-massive-hack-attack-on-gas-station-network-1090363581.html
https://sputnikglobe.com/20211028/hackers-breach-leak-personal-data-of-israeli-defense-ministry-servicemembers-emails-of-benny-gantz-1090265544.html
https://sputnikglobe.com/20211103/us-slaps-israeli-pegasus-spyware-developer-with-sanctions-1090455697.html
israel
united kingdom (uk)
Sputnik International
feedback@sputniknews.com
+74956456601
MIA „Rosiya Segodnya“
2021
News
en_EN
Sputnik International
feedback@sputniknews.com
+74956456601
MIA „Rosiya Segodnya“
Sputnik International
feedback@sputniknews.com
+74956456601
MIA „Rosiya Segodnya“
israel, hacking, middle east, united kingdom (uk)
israel, hacking, middle east, united kingdom (uk)
Hackers Reportedly Go on Global Hacking Spree Targeting Media, Governments Using Israeli Spyware
14:01 GMT 17.11.2021 (Updated: 15:16 GMT 28.05.2023) Israel’s US ally recently slapped sanctions on NSO Group – makers of the infamous spyware Pegasus, after the spyware was shown to have been used by governments to spy on world leaders, journalists, activists and opposition figures. Candiru, a lesser-known Israeli firm making programmes with functionality similar to Pegasus, was also blacklisted.
A computer hacking tool developed by Candiru, a Tel Aviv-based surveillance and cyberespionage technology firm catering to government clients, has been used to systematically attack websites in the UK, Iran, Syria and Yemen, ESET, a Slovak internet security company has discovered.
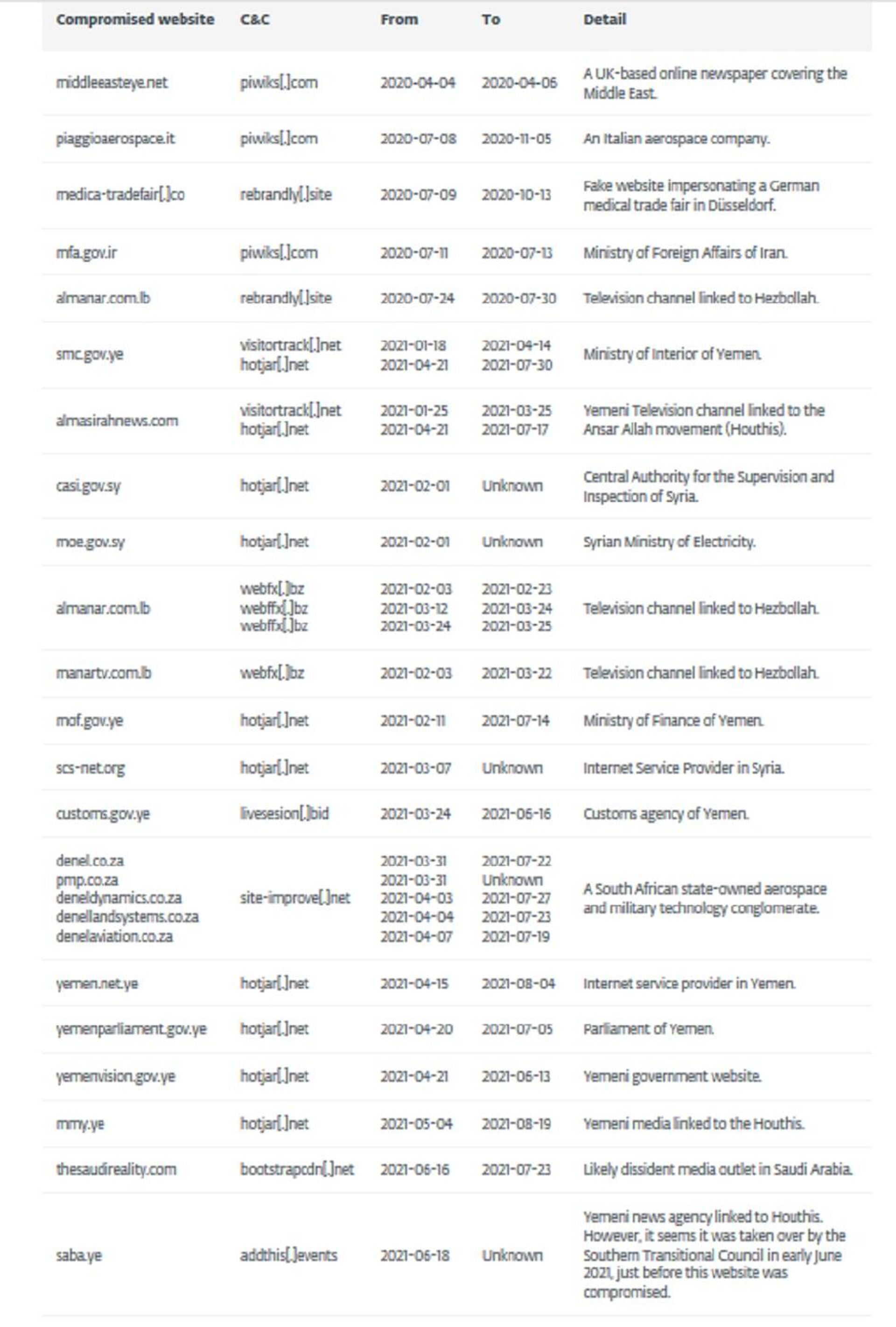
“The victimized websites belong to media outlets in the UK, Yemen, and Saudi Arabia, as well as Hezbollah; to government institutions in Iran (Ministry of Foreign Affairs), Syria (including the Ministry of Electricity), and Yemen (including the Ministries of Interior and Finance); to internet service providers in Yemen and Syria; and to aerospace/military technology companies in Italy and South Africa. The attackers also created a website mimicking a medical trade fair in Germany,” ESET said in a
comprehensive analysis published Tuesday.
The internet security company recorded a series of attacks between July 2020 and July 2021, when they suddenly stopped, with sites targeted using so-called ‘watering hole attacks’ – which involve attackers adding malicious code to websites’ JavaScript code to infect devices of “targets of interest” likely to visit them. The sites themselves are just “a jumping-off point to reach the final targets.”
The ultimate goal of the attacks were said to include collecting IP geolocation data and the targeted computer’s system information, and, if desired, to enable attackers to hijack the infected machines.
The affected websites include the Middle East Eye – a UK-based news site focused on Middle Eastern affairs, the site of Hezbollah’s Al Manar television channel, and Yemen’s Almasirah – a media outlet affiliated with the Houthis. thesaudireality.com, a Saudi dissident website critical of the monarchy, was also reportedly among those attacked.
Among other targets were Piaggio Aerospace, an Italian arms maker, and Denel, a South African aerospace and military tech giant.
Of the 21 websites attacked, eight are based in Yemen, three are Syrian, and three are operated by Hezbollah.
The Middle East Eye announced that it was
considering legal action against parties which it suspects of involvement in the attacks in the attacks, without elaborating on who it believes may be responsible.
In a report in July, the University of Toronto’s Citizen Lab software developer
reported, citing a lawsuit brought by a former Candiru employee, that the company’s clients include the governments of Saudi Arabia, the United Arab Emirates and Qatar, as well as Singapore and Uzbekistan.

31 October 2021, 11:45 GMT
In the wake of ESET’s reporting, a Candiru spokesperson
assured Forbes that the company itself does not carry out attacks on clients’ behalf, and that it does not have any knowledge about how clients use its tools. “The company is selling its products to government agencies only…the company and its product don’t hack websites,” the spokesperson said.
Candiru was founded in 2014, and is named after a parasitic catfish. The company is so secretive that it does not have public website, and little information exists online about its earnings, employees, and other basic information. The firm is only allowed to export its products
if Israel’s Defence Ministry grants it an export license.
The source or sources of the attacks are unclear. They reportedly ceased abruptly in mid-2021, after Citizen Lab researchers
issued a report on Candiru’s use by governments to target journalists and activists in Armenia, Iran, Israel, Lebanon, Yemen, Spain, the UK, and Turkey, and to have been operated from inside nations including Hungary, Indonesia, Israel, Saudi Arabia, and the United Arab Emirates.
“At the time of writing, it seems that the operators are taking a pause, probably in order to retool and make their campaign stealthier. We expect to see them back in the ensuing months,” ESET warned in its analysis.

28 October 2021, 01:53 GMT
The US Commerce Department surprisingly slapped Candiru and its more famous cousin, NSO Group,
with sanctions earlier this month. NSO Group’s Pegasus spyware, which can infect phones using ‘zero clicks’ (i.e. without any user interaction), and is impossible to remove, came into the public spotlight in July after the non-profits Forbidden Stories and Amnesty International shared a list of over 50,000 people whose phones were targeted. The software is capable of hijacking a phone’s camera and microphones, essentially turning it into a mobile spying device, and allows operators to access users’ contacts, message and call history, and more.
3 November 2021, 21:46 GMT
The victims of the military-grade spyware package reportedly included over a dozen world leaders, among them French President Emmanuel Macron, Iraqi President Barham Salih, South African President Cyril Ramaphosa, and others, as well as a bevy of former heads of state and government, UN and WHO officials, journalists, dissidents, and opposition politicians.
NSO Group defended itself by claiming that it sells its spyware to governments only for use against terrorists and criminals, suggesting that Pegasus had saved “tens of thousands of lives.” Instead, it was used by governments to target foreign adversaries and domestic opponents, with Mexican drug cartels also reportedly getting their hands on the software and using it to intimidate journalists.